Network Segmentation (retrofits)
Best Practice: This module details the technical execution of logical zone isolation (VLANs) and communication enforcement (ACLs). While IACS UR E26 is the standard for new-builds, this guide applies its core security logic to help existing vessels convert high-level “Zones and Conduits” theory into a deployable configuration for retrofitted OT networks.
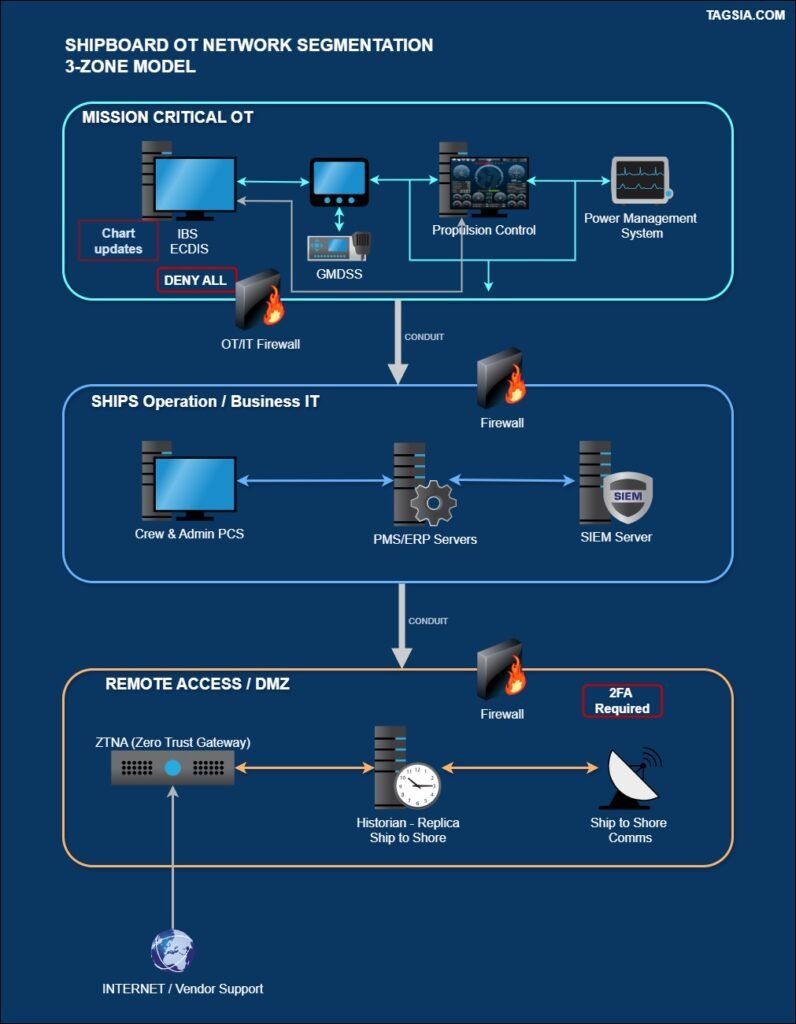
Network segmentation is the single most effective way to prevent an initial breach (e.g., a phishing email on the crew IT network) from disabling or seizing control of your critical Operational Technology (OT) systems.
This guide translates the foundational concept of Zones and Conduits from the IACS UR E26 and IEC 62443 standards into a three-step practical implementation plan for existing vessels seeking to retrofit zones for security compliance.
TAGSIA Tags: IACS UR E26 (3.1); IEC 62443-3-3 SR 1 (Zones & Conduits); IMO/ISM Code §11.2
The Core Concept: Zones and Conduits
Historically, many ships treated the entire network as one large, flat “trusted” zone. Segmentation divides this flat network into smaller, distinct Security Zones based on system criticality and security requirements.
- Security Zone: A collection of systems (assets) sharing the same security needs.
- Conduit: The secure communication path (firewall/ACL) enforcing rules between zones.
The Principle of Least Privilege: If a system doesn’t need to talk to another zone, the conduit must block it by default (Deny by Default).
Step-by-Step Implementation
For most vessels, a three-zone model is the most pragmatic starting point for compliance.
1 Zone 1: Mission-Critical OT (The Citadel)
- Assets: Bridge systems (ECDIS, Radar), Propulsion/PMS, Steering, Safety Systems.
- Requirement: Maximum Availability & Integrity. Air-gapped or Firewall-restricted.
- Action: Data must be brokered through a Stateful Firewall with a “Deny All” default rule.
2 Zone 2: Ship Operations / Business IT
- Assets: Admin (HR, Cargo), Crew Internet, CCTV, Inventory.
- Requirement: Standard IT controls. Susceptible to phishing.
- Action: Use VLANs to separate crew from admin and a firewall at the Zone 1 boundary.
3 Zone 3: Remote Access / DMZ (The Air Lock)
- Assets: ZTNA Gateways, Historian Replicas, SIEM, VSAT Comms.
- Requirement: High Protection/Low Trust.
- Action: External traffic lands at ZTNA. 2FA is mandatory for all entry.
Vessel Network Security Checklist
Use this checklist to verify that your segmentation strategy aligns with industry-standard cyber resilience practices found in IACS UR E26 and IEC 62443. This ensures your retrofit is robust enough to meet future insurance requirements and charterer expectations.
Retrofit Implementation Tip
When implementing this on an existing vessel, use 802.1Q VLAN tagging to create these zones logically if you cannot run new physical cabling to every deck. Ensure your core switch is “Managed” to support these boundaries and can handle the required Access Control Lists (ACLs).
Next Section
VLANs and ACL – 3-Zone Model
VLAN & ACL Configuration: Implementing the 3-Zone Model Requirement: This module details the technical execution of ...
